Most organizations are increasingly moving to digital platforms in order to benefit from developments in technology and increase their effectiveness and reach. Businesses can manage and expand more successfully as a result of the cloud’s continuous interaction with different networks. However, a secure cloud-based solution is required for a number of cloud-based cybersecurity challenges. The market currently offers Cloud Security Posture Management (CSPM) products for locating compliance problems in cloud architecture. And Lacework, which is the best for Cloud Security Posture Management Solution.
Contents
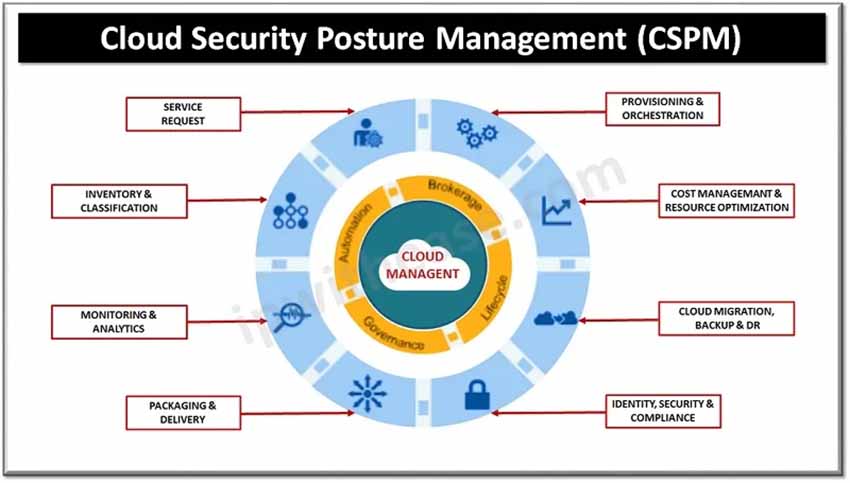
What is Cloud Security Posture Management (CSPM)?
Infrastructure as a Service (IaaS), Software as a Service (SaaS), and Platform as a Service (PaaS) are just a few examples of cloud infrastructures where Cloud Security posture management (CSPM) automates the discovery and remediation of vulnerabilities (PaaS). With the help of CSPM, risk visualization and assessment, incident response, compliance monitoring, and DevOps integration can all be done in hybrid, multi-cloud, and container environments while applying uniformly good cloud security practices.
Why Lacework is the best for Cloud Security Posture Management Solution?
What is Lacework?
The Polygraph Data Platform of Lacework, a cloud security platform, automates cloud security at scale for clients to develop quickly and safely. The only security platform that can gather, examine, and precisely correlate data from an organization’s AWS, Azure, GCP, and Kubernetes environments, as well as distill it to just a few critical security events, is called Lacework.
As a tool for breach detection and investigation, Lacework offers details on when and how a breach occurred, as well as the people, devices, and applications involved. The system can automatically learn what is typical for your surroundings and identify any anomalous behavior by utilizing machine learning and behavioral analytics. Furthermore, Lacework provides you with ongoing access into your cloud environment so you can see vulnerabilities, incorrect configurations, and malicious activities.
The benefits of CSPM Lacework
Implementing Lacework has a lot of advantages. The following are some of the solution’s greatest benefits:
- For greater security management, gain comprehensive observability into your cloud accounts, workloads, and microservices.
- Threat detection: Lacework enables your business to immediately respond to common security events that target your infrastructure-as-a-service (IaaS) accounts, containers, and cloud servers.
- Flexible deployment: Lacework gives you the freedom to deploy in the agent or agentless fashion of your choice, giving you the visibility required to have the highest level of security for cloud accounts and systems. You quickly realize value because Lacework provides a tiered strategy that is simple to deploy.
- Configuration compliance: Using the Lacework solution, you can quickly discover non-compliant IaaS account setups and spot chances to implement security best practices.
- Synced teams: Regardless of the size or expertise of your team, Lacework enables your teams to work more efficiently and close the gap between security, development, and operations.
- Gain insightful security information: Lacework offers insightful security information, warning you of problems from your current workflows before they reach production. You may create apps rapidly and with confidence in this way.
- Higher revenue streams: They are made possible by the solution’s security features, which were integrated into it from the very first line of code.
- Prevents development delays: By providing DevOps and security teams with access to security information for earlier risk mitigation that speeds innovation, the Lacework solution aids in improving your ability to prioritize security solutions.
- Productivity growth: Lacework avoids data silos and expensive investigations while providing warnings with all the context you require, allowing you to increase productivity.
- Contextualize and correlate behaviors:Lacework can combine characteristics and information from your particular environment to create actions.
- Cloud security posture and compliance streamlined: You may decrease risks and meet compliance standards with the Lacework platform’s extensive visibility and ongoing tracking, which will boost your bottom line.
- Resolve weaknesses before it’s too late: By using lacework, you may reduce your attack surface and fix the riskiest vulnerabilities as early as possible in the development cycle.
How does Cloud Security Posture Management work?
Cloud Security Posture Management offers continuous threat detection, misconfiguration management and remediation, discovery and visibility, and DevSecOps integration.
Finding and Recognition
The cloud security configurations and infrastructure assets are discovered and made visible by CSPM. A single source of truth is accessible to users across several cloud environments and accounts. Upon deployment, cloud resources and details, such as configuration errors, metadata, networking, security, and modification activity, are immediately found. A single console is used to administer security group policies for accounts, regions, projects, and virtual networks.
Management of Misconfigurations and Their Correction
By comparing cloud application configurations to industry and organizational benchmarks, CSPM reduces security risks and speeds up the delivery process so that violations may be found and fixed in real time. Guardrails are offered to assist developers in avoiding errors. Misconfigurations, open IP ports, illegal alterations, and other problems that expose cloud resources can be rectified with guided remediation. Storage is watched over to ensure that the right permissions are always in place and that no data is ever unintentionally made public. Additionally, database instances are watched to make sure encryption, backups, and high availability are enabled.
Detection of threats continuously
Through a targeted approach to threat identification and management, CSPM actively detects risks throughout the whole application development lifecycle by sifting through the noise of multi-cloud environment security warnings. The CSPM prioritizes vulnerabilities depending on the environment, concentrates on the places adversaries are most likely to exploit, and prevents vulnerable code from entering production, all of which lower the amount of warnings. Using real-time threat detection, the CSPM will also continuously monitor the environment for malicious activity, unauthorized activity, and unauthorized access to cloud services.
Integration of DevSecOps
By removing friction and complexity across several cloud providers and accounts, CSPM lowers administrative costs. Agentless posture management that is native to the cloud offers centralized visibility and control over all cloud resources. Security teams can prevent compromised assets from moving through the application lifecycle thanks to a single source of truth provided by security operations and DevOps teams.
In order to improve visibility and gather details and context about incorrect setups and policy breaches, the CSPM should be linked with the SIEM.
In order to provide quicker repair and reaction inside the DevOps tool set, the CSPM should also interact with existing DevOps tool sets. The infrastructure, DevOps, and security operations teams can all comprehend each other’s perspectives thanks to reporting and dashboards.
Conclusion
It is challenging to maintain visibility across public cloud accounts, likely across numerous public cloud vendors. Numerous thousands of cloud resources that have been deployed need an automated audit and mitigation method. In contemporary cloud computing systems, a Cloud Security Posture Management (CSPM) provides visibility into risk and compliance posture. Automating cross-account audits and resolving configuration issues prevents them from being misused.






